- We provide the best security services to protect your IT assets through the integrated IT security.
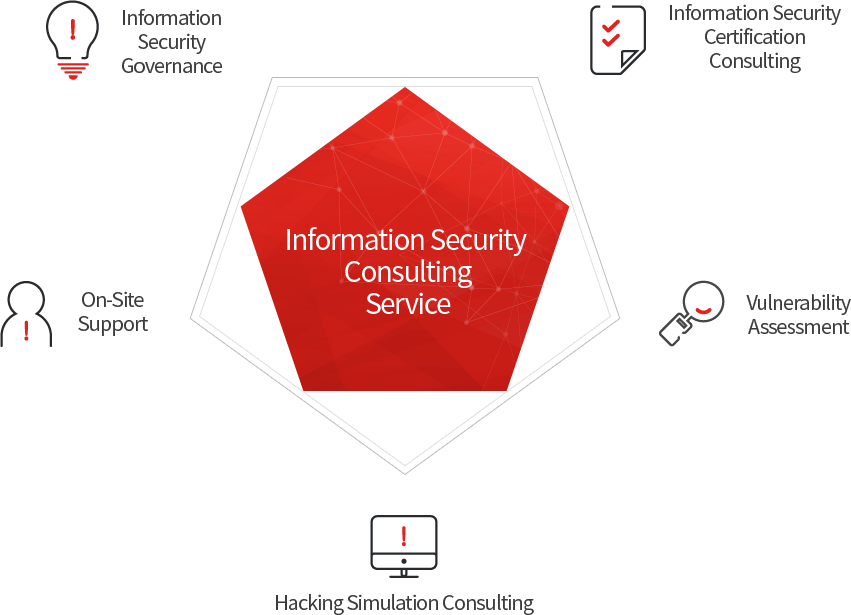
Information protection consulting protects your IT assets through technology assessment and hacking simulation, various information security certification consulting, annual security inspection and consultation, information protection service, and etc.
and attainment of internal and external reliability
- Information security governance
- Infrastructure vulnerability assessment (OS, DB, WEB, etc.)
- Hacking simulation
- Information security certification consulting
- ISMS, ISO27001, PIA, PIMS, PIPL, etc.
- Personal Information Retrieval and Centralized Management Solution
- Worm Storage for SOHO (Prevention of forgery, altering, and unauthorized deletion of major assets)
- SCADA dedicated media control solution
- Anti Virus solution
- IBM Qradar Partner Registration
- Web, email, DLP security
- ICS Security (AnD for SCADA)
- Multi-Antivirus Scan / Defender
- APT detection solution
Information Security Governance
We contribute to your value creation by presenting optimal management scheme for your IT resources in five major specialized areas to continuously improve and upgrade the information security management system that fits the corporate environment.
 Performance Management
Performance Management- KPI measurement and monitoring
- Performance analysis and adjustment
- Risk management utilization and interlink with standard IT operation system
 Resource Management
Resource Management- Efficient and effective operation of information security resources
- Reduction of cost through establishment and optimization of standardized process
 Risk
RiskManagement
- Value identification and risk assessment of information assets
- Establishment of response strategies based on value
- Interlink of standard based IT operation management and risk management
 Value
ValueManagement
- Support business objectives
- Reduction of operation and development cost through standardized optimization
 Strategy Management
Strategy Management- Interlink of business objectives and information security activities
- Information security strategy lifecycle management
- Redefinition with business terminology
- Definition of CSF and KPI
Information Security Certification
It provides information security management system such as security policy/organization and risk management as security consulting methodology, and enhances the external image/reliability of the company and security level through information security certification.
BCM(Business Continuity Management)
This is an overall management process to provide a framework to establish resilience of the organization in order to ensure continuity of work when potential threats emerge to operations corporate-wide
ISMS, PIMS, PIPL, PIA
Continuous improvement of security level through systematic protection of important information and personal information according to the standard of each certification
Major Info-communication Infrastructure
Perform comprehensive risk assessment such as periodical checking of managerial/physical/technical vulnerabilities and hacking simulation.
ISO27001:2015
System designed to sustain the PDCA model for the information security management system required by the ISO 27001 standard
Technical Vulnerability assessment
The technical vulnerability assessment analyzes and evaluates weaknesses in the IT infrastructures of companies and provides customer service availability through the establishment of a more safe and effective information security management system.
Web Application
- Web vulnerability assessment
- Web hacking simulation
- Source code assessment
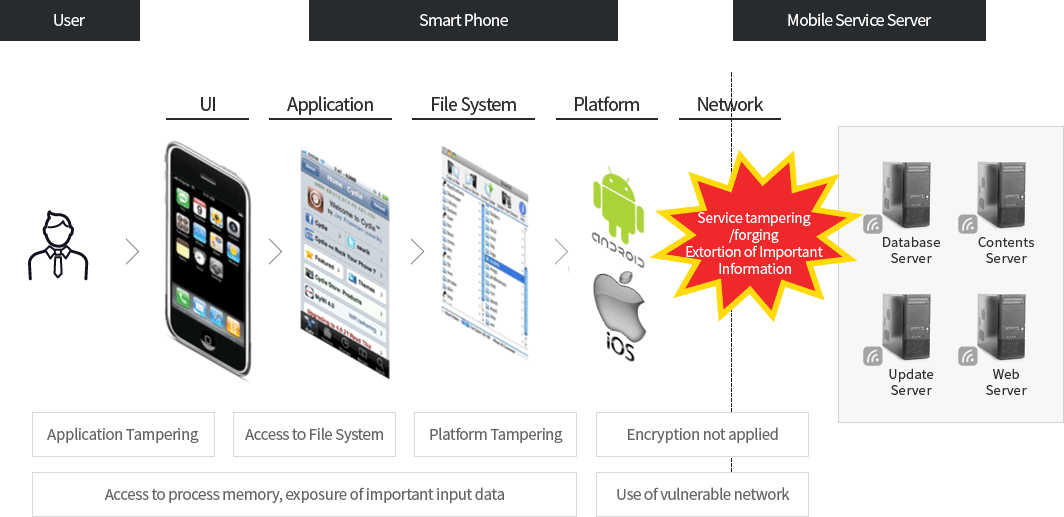
Mobile assessment
- Mobile vulnerability assessment
- Information leak risk assessment
- Source code assessment
Information Security System
- Security Policies assessment
- Access privilege management assessment
Server
- OS vulnerability assessment (Windows, Linux, Unix, etc.)
- Web/Was vulnerability assessment (Apache, IIS, WebtoB, Jeus, Tomcat, WebLogic, etc.)
Network Equipment
- Setting status assessment
- Security setting assessment
Hacking Simulation
It identifies possible vulnerabilities of web/mobile applications and performs scenario-based inspection by professional hacking simulation personnel and provides protection measures.
- 01 Web App Assessment Manual assessment by professional hacking simulation personnel
- 02 Mobile App Assessment Identification of possible vulnerabilities in smartphone and wireless network environments
- 03 Establishment of improvement plans Establishment of corrective measures for each vulnerability and security guide
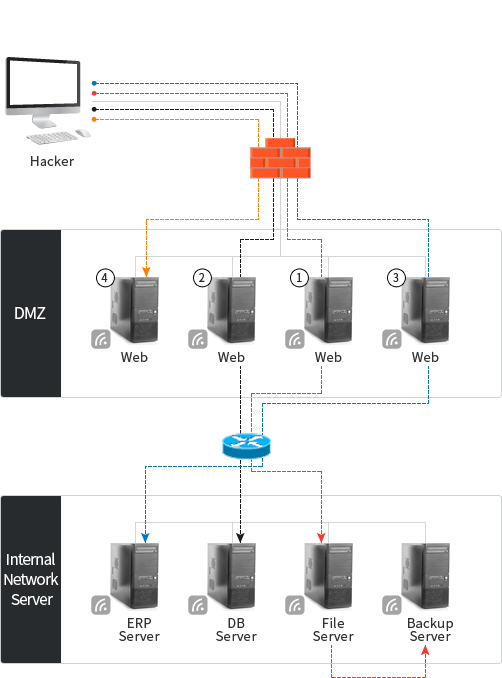
- Possibility of penetration and taking over the system
- Penetration to DB server and File server of internal network through acquiring data of the internal network server by penetrating the web server
- Possibility of accessing the DB and leaking personal or important information
- Extortion of personal information or important information through the weak points of the SQL Injection of homepage
- Extortion of personal information and important information of DB after uploading WebShell of web server
- Possibility of checking and leaking important information of the internal network from external networks
- Check accessibility of internal network server after penetration of Web server (DMZ)
- Extortion of internal important information after penetration of internal system using tunneling technique
- Manipulation of transaction amount
- Transaction amount manipulation by bypassing transaction process
- Bypassing final transaction amount through manipulation of coupon discount price
- Bypassing transaction amount using another user's E-Money
On Site-Support
We contribute to the improvement of security level by providing comprehensive security services such as incident response, security audit, security training, expert service, and etc.
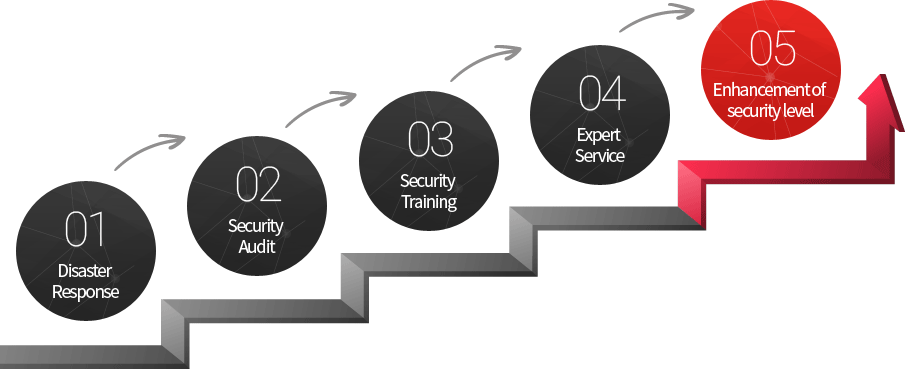
Establishment of mutual cooperation and coordination system among response teams Effective prevention, response, recovery, and follow-up of intrusion attempts
Strengthen compliance with related laws and corporate security policiesPrompt resolution of identified items and awareness of security responsibilities
Successful management of changes in employee security awareness, maturity of organizational security, and enhancement of expertise of security officer
Annual consulting contract enables immediate resolution of internal issues, ensuring continuity of security operations
SI / NI
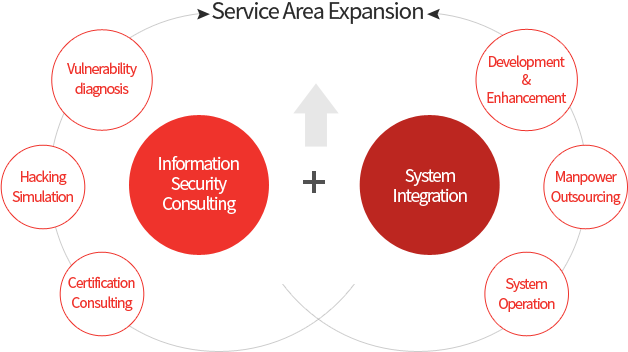
SI, and NI business support planning, designing, construction and actual operation of information systems suitable for market and customer needs.
System Integration
SI Sector
- System enhancement through infrastructure vulnerability diagnosis
- Personal information retrieval centralized management solution
- WORM Storage and USB Blocking Solutions
- System operation and maintenance
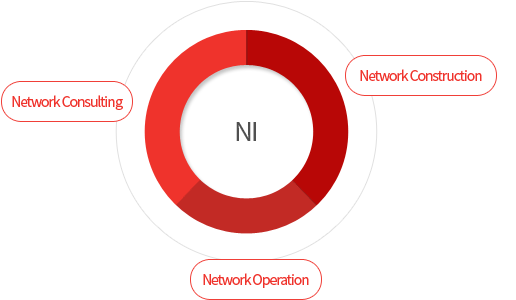
Network Integration
NI Sector
- Customized infrastructure planning, design and establishment of master plan
- Construction of network and security equipment infrastructure
- Help desk operation for management, performance management, fault handling
Major Accomplishments
We provide a variety of information protection services, including over 100 items of information protection consulting, security solution development and construction for major public organizations and corporations.






















































